With the new year in full swing, there’s a lot of conversation around what comes next and what 2020’s impact will mean for 2021. IT teams, specifically, are working to understand how to get a grip on content sprawl in the era of remote work. A recent study surveyed 400 IT leaders to understand how COVID-19 has impacted businesses’ ability to maintain data security and governance with a distributed workforce.
Results from the report underscore the challenges with on-prem-first strategies in a work-from-anywhere world. Companies rushed to the cloud to support business-as-usual, but are now dealing with the impact of content growing and spreading across more applications, more users, and more devices than ever. CIOs reported that this sprawl is not only creating inefficiencies and driving up costs, but that it is introducing new and greater data security risks.
With an average of 47% of corporate files containing sensitive data, it’s no surprise that the increased risk of data breaches is the top concern for CTOs when it comes to content sprawl.
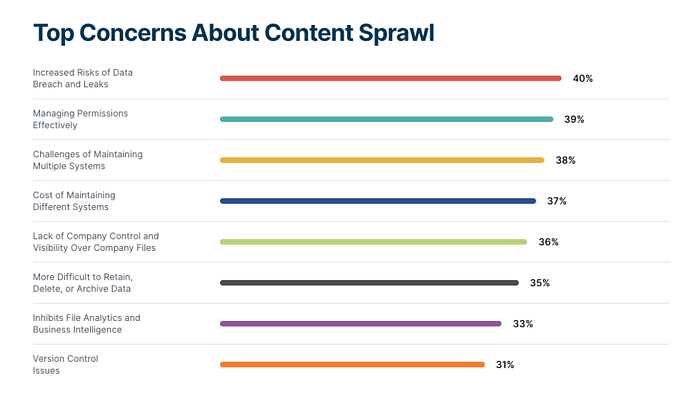 A well-educated and well-informed workforce is one of the best defenses against security risks. However, 71% of survey respondents think that their employees could do better to protect sensitive data, and 62% reported Employee Carelessness as their top data security concern.
A well-educated and well-informed workforce is one of the best defenses against security risks. However, 71% of survey respondents think that their employees could do better to protect sensitive data, and 62% reported Employee Carelessness as their top data security concern.
This is why CIOs are implementing new protocols in hopes of keeping their data safe in the remote-work era.
But new protocols and risk mitigation measures alone won’t be enough to address the risks and realities of the future of work. IT executives are also implementing new data use policies, deploying artificial intelligence, centralizing content, and restricting unauthorized apps.
These measures are about operationalizing security at scale while maintaining productivity so that users have secure access to the data they need to work and collaborate from anywhere.
Five Recommendations for Operationalizing Security for Productivity and Governance:
Inventory Your Data:
Know what you have, who has access to it, and where it is. A comprehensive scan of unstructured data stores can provide visibility into the highest-value data, which most often represents the biggest risks. And once you know where your high-risk issues are, you can start doing something about it: locking down access, cleaning up permissions, and removing stale data that’s outlived its value. Not knowing is simply no longer an option.
 Stop Manual Tagging:
Stop Manual Tagging:
For too long, end-user tagging has been the primary means by which most companies classify files that contain sensitive, proprietary, or regulated data. The sheer volume of data regulations is impossible for end-users to keep track.
With the amount of sensitive data buried inside of documents, end-user classification should not be your company’s compliance engine or security backstop. There is too much at stake. Training end-users is great, but use it as a signal and not a source of truth.
Leave Legacy Servers Behind:
Get rid of non-sanctioned apps and servers that are vulnerable to hacks. Get away from common vulnerabilities and get behind a solution that is centrally managed and monitored 24 hrs a day.
Enable Controlled Sharing:
Deploy user-friendly collaboration with robust governance controls. The more integrations available, the more offline access and the easier it is to share and collaborate in real-time, the better.
Provide the correct sharing options, and only the correct sharing options, to users based on the data itself. The more seamless these controls are, the better the user experience and the less likely users will be to circumvent them.
Circumvention leads to shadow IT, risky workarounds, and using personal email to transmit data, all of which exacerbates sprawl and makes visibility and control more difficult.
Assess Governance:
Governance is a cultural skill. Enlist data owners to become guardians. This is about risk reduction over time. Governance is not coming and going. Regulations are not going away.
This means that you cannot rely on just one or two administrators. They’ll be overburdened and overwhelmed. Delegating and deploying tools that empower line of business users to own their team’s data handling practices, and monitor and enforce them will be essential going forward.
This is not a one-time thing, and governance is the key to starting this process.
Governance for Business Growth
As IT leaders, it’s our job to care for this data. Your data is the value.
Individuals and customers are demanding better privacy and control over personal data. And larger enterprises are increasingly scrutinizing the data security practices of companies they partner and contract with. Caring about this is not just about avoiding risk. It’s about the growth and future of your business.
Don’t think about governance as a project. Think about governance as the first step to becoming a data-driven business.
How to start
InfoDNA Solution’s professionals and tools can bring an immediate answer to how big the problem is for an organization – no matter the current landscape of technologies. Topla, by InfoDNA, can analyze any mix of technologies and extract knowledge that may otherwise me missing automatically. Learn more from www.infodnasolutions.com